Digital Twins (DT) have revolutionized industrial processes, especially incident detection and incident response in industrial environments. By replacing trial-and-error with simulations, Digital Twins minimize waste and optimize processes through data analysis. The extension of the cyber physical systems CPS like analyzed in Zero-SWARM and the use of different frameworks in industrial control systems offer new ways to interact with devices and meet real-time demands.
A Growing Security Challenge
Industry 4.0 blurs the lines between IT and OT, increasing the need for interconnected OT networks and robust cybersecurity. Industrial software libraries and industrial protocols, such as Modbus, EtherNet/IP, ROS or other industrial protocols often lack built-in security, creating vulnerabilities that attackers can exploit. This may lead to serious consequences at the industrial level, such as damaging equipment, halting production, or even compromising the safety of operators.
Incident Response by Zero-SWARM
To prevent these issues, organizations need well-planned incident response (IR) and threat intelligence (TI) services. In the context of the Zero-SWARM project has created a cyber kill chain for industrial production systems has been modelled using the MITRE ATT&CK Framework. A cybersecurity detection and response system, as detailed in figure 1 below, has also been developed to mitigate the detected attacks and reduce the damage on the industrial environment.
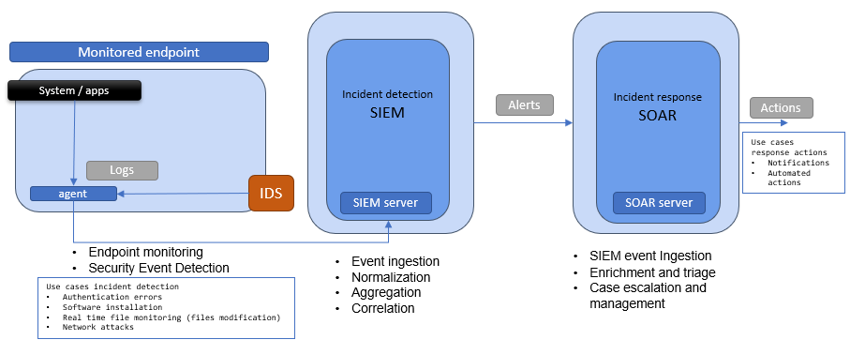
Figure 1: Incident detection and Incident response workflow
Cyber Kill Chain in OPC-UA Industrial Environments
A cyber kill chain is a series of steps attackers use to compromise a target. Zero-SWARM defined a cyber kill chain for OPC-UA industrial environments to test and simulate offensive OT scenarios.The steps are as follows:
- Reconnaissance stage: Discover the network using tools like nmap to identify hosts, services, and the OPC-UA communication source.
- Privilege Scalation stage: Launch attacks like brute force using Metasploit.
- Cyber Intrusion stage: Modify OPC-UA server parameters or disrupt the service.
Strengthening Industrial Cybersecurity
Adhering to IEC 62443-3-3 security standards is crucial for protecting industrial processes. Continuous monitoring, a foundational requirement, helps identify and respond to threats.
SIEM and SOAR solutions can collect logs, generate security events, and automate incident response actions. These tools will help to be aware of the possible cyber kill chains affecting the system, and to be prepared to detect and mitigate the attacks as soon as they occur. By combining cyber threat intelligence with SIEM and SOAR, organizations can enhance alert prioritization, execute automated mitigations, and improve overall effectiveness in incident detection and incident response in industrial environments.
Want to learn more about these technologies? Book a call with our experts here and join the Zero-SWARM community to continue discussing this topic. For more information about cybersecurity and Threat Intelligence in Industrial, see the following references:
- Hearn, M., & Rix, S. (2019). Cybersecurity considerations for digital twin implementations. IIC J. Innov, 107-113.
- Incident Response & Threat Intelligence – Guidepoint Security: https://www.guidepointsecurity.com/incident-response-and-threat-intelligence/

